OVERVIEW
GOSECRETSRESORTS.COM TRAFFIC
Date Range
Date Range
Date Range
GOSECRETSRESORTS.COM HISTORY
WEBSITE SPAN
LINKS TO WEBSITE
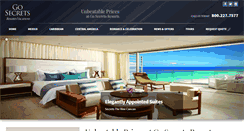
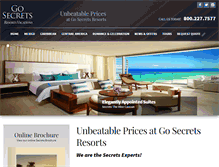
WHAT DOES GOSECRETSRESORTS.COM LOOK LIKE?

CONTACTS
A Way To Go Travel
Chuck Joyce
4205 C West Wendover Ave
Greensboro, North Carolina, 27407
United States
GOSECRETSRESORTS.COM SERVER
NAME SERVERS
WEBSITE ICON

SERVER SOFTWARE
We observed that this website is weilding the Microsoft-IIS/8.5 server.SITE TITLE
Go Secrets ResortsDESCRIPTION
Go Secrets ResortsPARSED CONTENT
The domain gosecretsresorts.com had the following on the web site, "Punta Cana, Dominican Republic." I analyzed that the website said " World Class Spa by Pevonia." They also stated " Secrets Maroma Beach Riviera Cancun. Say I Do in Paradise. Secrets Maroma Beach Riviera Cancun. View our online Secrets Brochure. Unbeatable Prices at Go Secrets Resorts. We are the Secrets Experts! We are the Secrets Resorts experts ready to assist you in planning your next getaway! We pride o."SEE OTHER WEBSITES
What is Section 8? Fair Housing and Equal Opportunity. You are now leaving the. Site and being redirected to GoSection8. Find a great place to live with the largest affordable housing listing service in the nation - whether you have a section 8 voucher or are just looking for a good deal.
Managed Services for IT Security Operations. Architecture, Analysis, Deployment and Support for Technical Security Solutions. IT Strategic Planning and Governance. Risk Assessment, Design and Audit of IT Controls. Managed Services for Client, Server and Mobile Endpoint. Logical and Physical Security Control Testing through Social Engineering. Around the clock emergency number.
Leakage of your company-sensitive information to competitors may be not only irritating, but also devastating to business.
Security technology and process roadmap. Perimeter defense and Intelligence driven SIEM. A heightened level of detection and defense against the most sophisticated type of security threats those that come from an Advanced Adversary.
Насколько уязвим ваш бизнес и вы сами, когда кто-то посторонний имеет возможность доступа к вашей информации? Что сделают ваши конкуренты, контролирующие органы, журналисты, недруги и мошенники, получив конфиденциальную информацию о вашем бизнесе? Защита информации на дисках компьютера от несанкционированного доступа.